Monitoring Docker Container Logs
Docker is a containerisation technology that enables the creation and use of both Linux or Windows containers. They are extremely lightweight and can be easily created, deployed, copied or moved from environment to environment.
In this blog we will be looking at collecting container logs.
Install Docker CE following Docker's Docs for Centos: https://docs.docker.com/v17.09/engine/installation/linux/docker-ce/centos/
Create a user for Docker and add the user to the Docker group
Setup a HTTP Event Collector on a Splunk instance (See Installing Splunk)
A HTTP event collector allows you to send data and application events to a Splunk deployment over HTTP/HTTPS, further reading: https://docs.splunk.com/Documentation/Splunk/7.3.1/Data/UsetheHTTPEventCollector
Enable HEC through Global Settings:
1. Click Settings > Data Inputs
2. Click HTTP Event Collector
3. Click Global Settings
4. In the All Tokens toggle button, select Enabled
5. Uncheck the Enable SSL checkbox
6. Leave the rest of the settings as default
Configure a HEC token:
1. Click Settings > Add Data
2. Click monitor
3. Click HTTP Event Collector
4. In the Name field, enter a name for the token
5. Click Next
6. Leave the default options for the Input Settings
7. Click Review
8. Click Submit
9. Make a note of the HEC token value
Setup the Splunk Logging Driver on your Docker Host
The Splunk logging driver sends container logs to HTTP Event Collector in Splunk, further reading: https://docs.docker.com/config/containers/logging/splunk/
1. Create daemon.json under /etc/docker
Now we can look at collecting Docker Metrics
In this blog we will be looking at collecting container logs.
Install Docker CE following Docker's Docs for Centos: https://docs.docker.com/v17.09/engine/installation/linux/docker-ce/centos/
Create a user for Docker and add the user to the Docker group
sudo useradd docker_user && sudo usermod -aG docker docker_userSwitch user and then start Docker
sudo systemctl start docker
Setup a HTTP Event Collector on a Splunk instance (See Installing Splunk)
A HTTP event collector allows you to send data and application events to a Splunk deployment over HTTP/HTTPS, further reading: https://docs.splunk.com/Documentation/Splunk/7.3.1/Data/UsetheHTTPEventCollector
Enable HEC through Global Settings:
1. Click Settings > Data Inputs
2. Click HTTP Event Collector
3. Click Global Settings
4. In the All Tokens toggle button, select Enabled
5. Uncheck the Enable SSL checkbox
6. Leave the rest of the settings as default
Configure a HEC token:
1. Click Settings > Add Data
2. Click monitor
3. Click HTTP Event Collector
4. In the Name field, enter a name for the token
5. Click Next
6. Leave the default options for the Input Settings
7. Click Review
8. Click Submit
9. Make a note of the HEC token value
Setup the Splunk Logging Driver on your Docker Host
The Splunk logging driver sends container logs to HTTP Event Collector in Splunk, further reading: https://docs.docker.com/config/containers/logging/splunk/
1. Create daemon.json under /etc/docker
sudo touch /etc/docker/daemon.json && vi /etc/docker/daemon.json2. Paste in the following replacing
{3. Restart Docker to apply the changes
"log-driver": "splunk",
"log-opts": {
"splunk-token": "<HEC TOKEN>",
"splunk-url": "http://<SPLUNK SERVER>:8088",
"splunk-insecureskipverify": "true",
"splunk-format": "inline",
"tag": "{{.ImageName}}/{{.Name}}/{{.ID}}"
}
}
systemctl restart docker4. Spin up an NGINX container as the docker user
sudo su docker_user5. Send a curl request to localhost
docker run --name nginx -h nginx -p 80:80 nginx
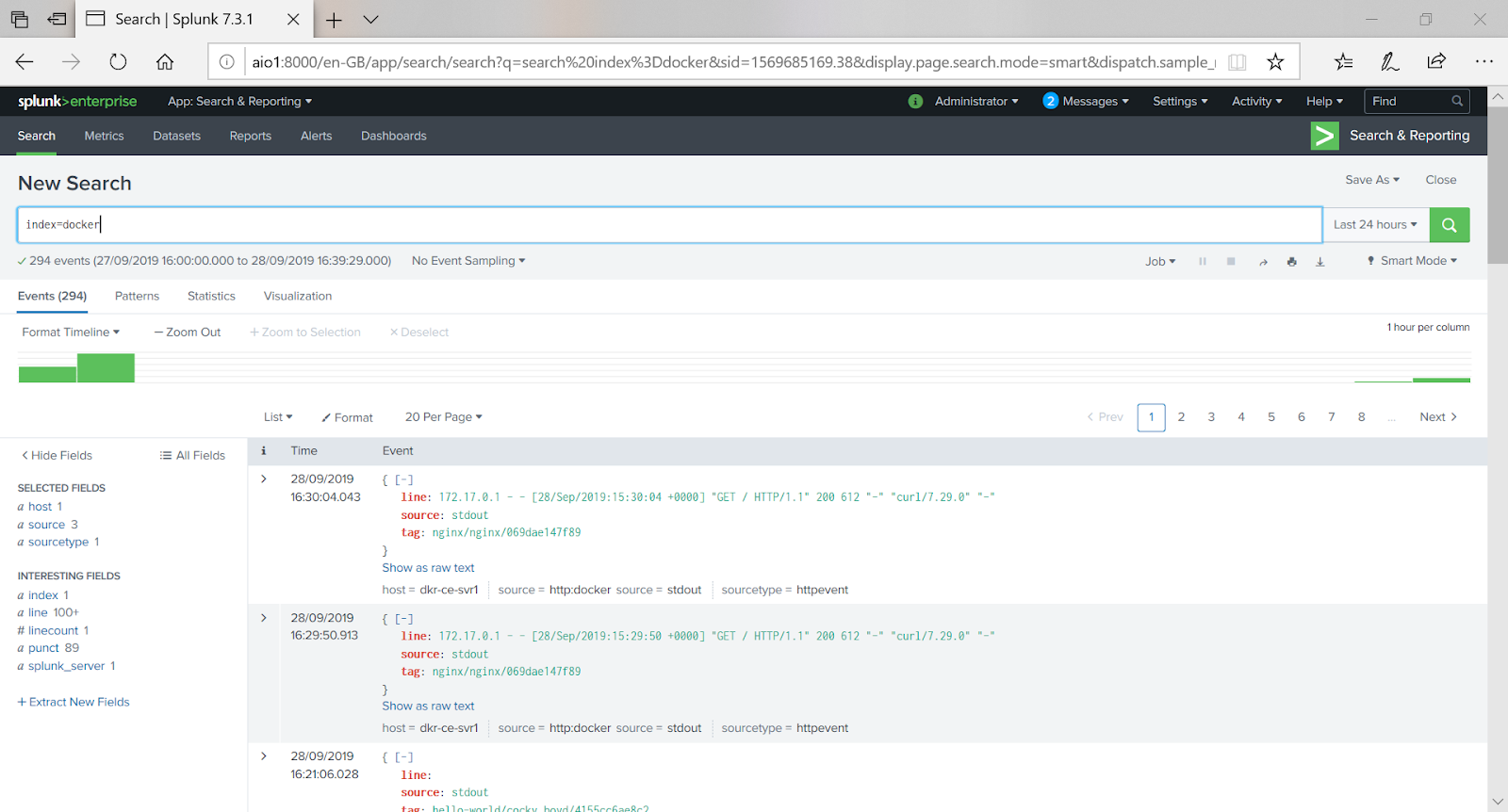
curl localhostLog onto Splunk, under Apps click on Search and Reporting, run a search on the main index and you should now see NGINX logs.
Now we can look at collecting Docker Metrics

Comments
Post a Comment